If you’re familiar with the password recovery tool Hashcat you’ll know that the default go to is the GPU version, oclHashcat.
A quick demonstration of why you don’t bother using the CPU version of Hashcat any more. First up, the Hashcat benchmark against md5crypt with 16CPUs on a “grunty server”.
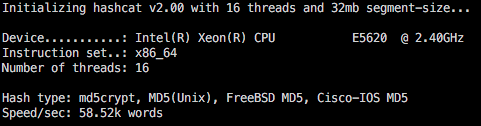
The benchmark shows a capability on this setup of 58,000 brute force attempts per second. While this will get you started, it means once you are recovering passwords beyond 5 or 6 characters, your time for recovery is going to be weeks/months/years.
And now I run the same benchmark using oclHashcat, this time using an Asus gaming laptop which is about a year old, and has a nVidia GTX950 graphics card.
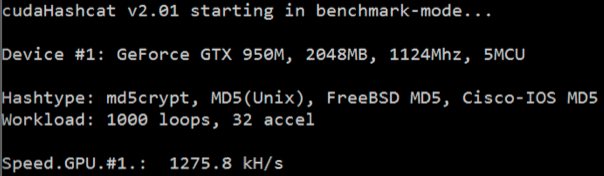
This time the benchmark shows we can get 1,275,000 attempts per second, roughly a 20x improvement which means your recovery time will be significantly shorter :-)
Each crypt type will have different base results on the per second attempts, some are far quicker than md5crypt, however I have found the hash improvement ratio between CPU/GPU to be similar across crypt types.
The per second value can increase even further if you are using a newer, faster GPU, instead of the older GPU in the laptop I used for this test.